
Image: YouTube

Like snapping selfies? Here's something to consider next time you mug for the camera: hackers.
Germany's biggest hacker group, the Chaos Computer Club, demonstrated just how easy it is for someone to break through the four most common types of computer protection.
Speaking to an enthusiastic audience at a cybersecurity conference in Hamburg late last month, the keynote speaker (identified only as "Starbug" and sporting a black hoodie with the word "terrorist" emblazoned across the front) showed how unsecured computers and cellphones really are, despite seeming protected with passwords, lock codes, fingerprint scanners, facial recognition systems or even iris scanners.
As Starbug demonstrated, a hacker doesn't even have to be in the same room as the victim to swipe their information.
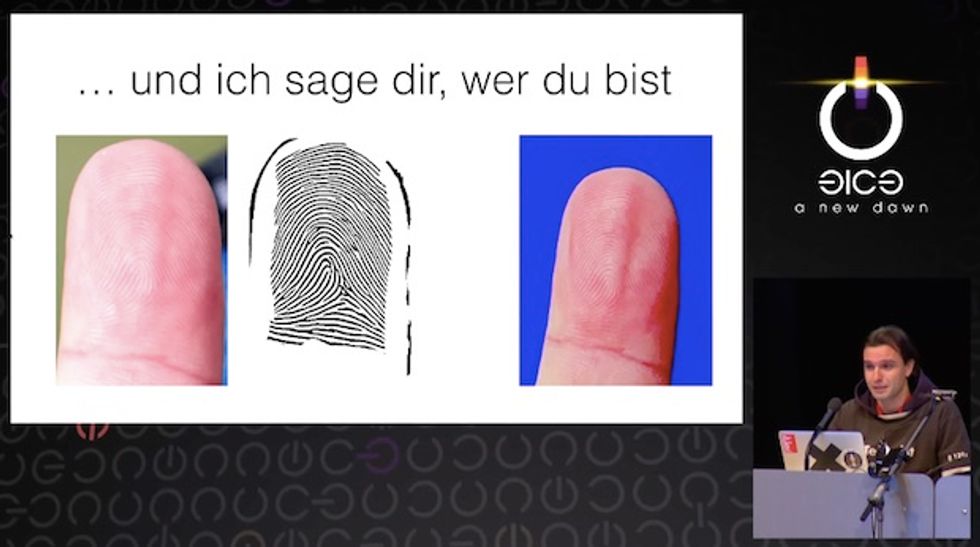
He showed how photographs posted online can be used to recreate the fingerprints of an unsuspecting victim. Once captured, prints can be recreated and used to unlock an iPhone with a thumbprint scanner, a computer with a fingerprint lock system, or even a gun safe that relies on a fingerprint to gain access.
Fingerprints can be grabbed from virtually anywhere, he said, quipping: "If you ever want to write a ransom letter...wear a pair of gloves."
Starbug was the winner of a contest to break through Apple's security system. A group called "Is Touch ID Hacked Yet?" put out the challenge, and paid the winner in bitcoins.
See his video of the demonstration:
And for the selfie generation, there's this: if you put your stock in a security code to protect your code, be aware. Check out the reflection of the person's phone reflected in their eye:
 Image source: YouTube
Image source: YouTube
A closer examination of the keypad suggests it's possible to see which numbers were tapped to unlock the phone. Just by identifying which digits had the greatest number of fingerprints, patterns and possible lock codes were easily identified.
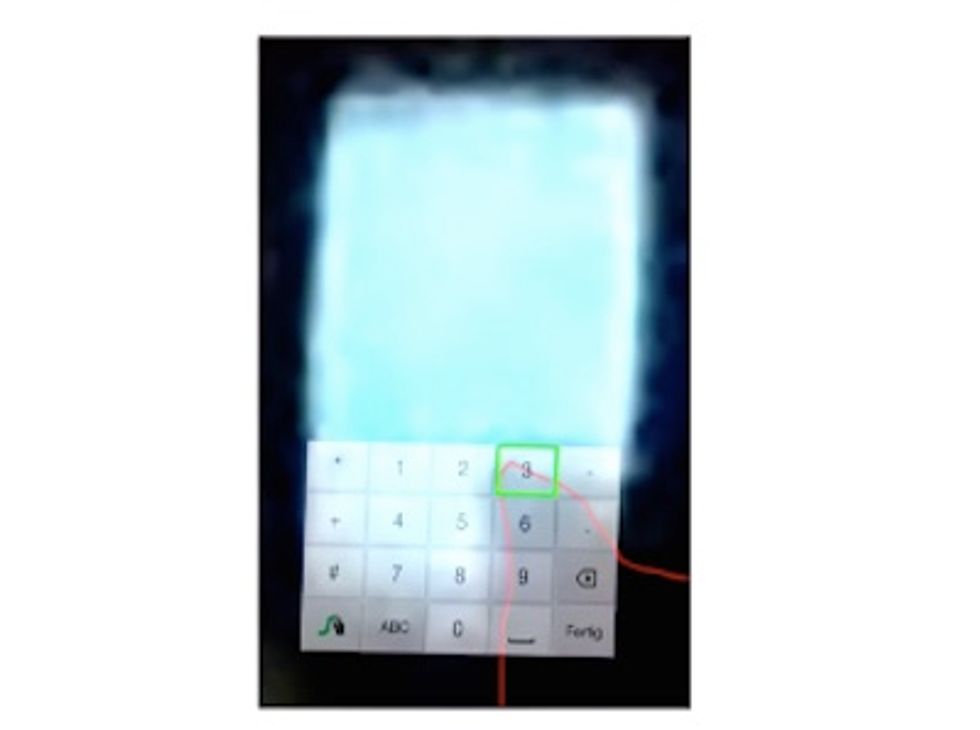
Starbug told the audience their first few attempts to figure out the code were unsuccessful. However, because most cellphones allow multiple unlocking attempts before shutting down, the hackers were able to get through the locking code about 90 percent of the time.
In another example, he demonstrated how a photograph of a person's face could fool a basic iris scan.

A printed photograph was held up to an iris scanner and actually fooled by the image.

The presentation also included an example of how the new, high resolution photos used in political advertising could be a source from which to lift the identity of leaders like German Chancellor Angela Merkel. These images offer both the potential to create an iris scan and when hands are visible — a duplicate fingerprint.
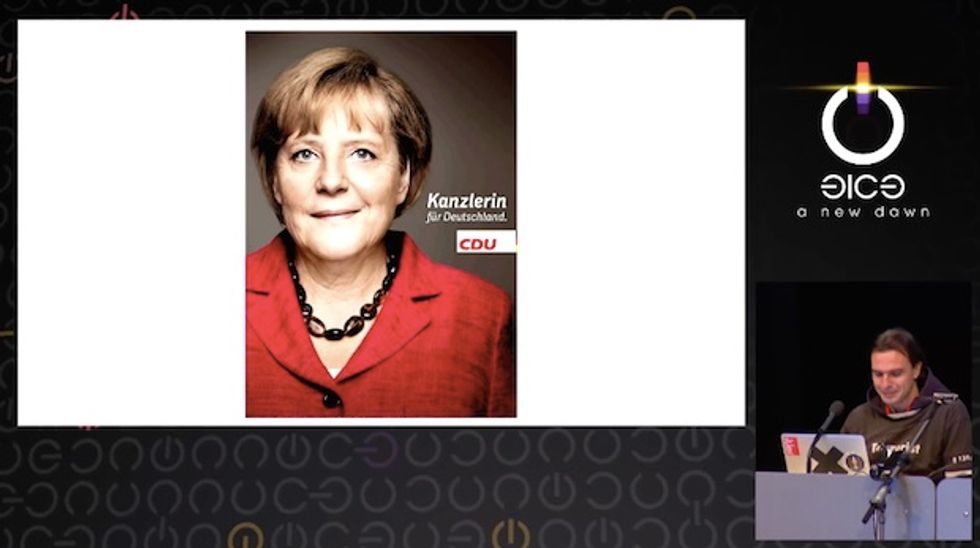
While talking about maintaining a secure computer or cellphone, Starbug declared the improving resolution on smart phone cameras to be "dangerous to this process."
While promoting the event, the Chaos Computer Club's website predicted: "After this talk, politicians will presumably wear gloves when talking in public."
Watch the entire keynote from the Dec. 27 meeting:
—
Follow Mike Opelka (@Stuntbrain) on Twitter.